System Fundamentals
1.2 System design basics (10 hours)
by M Brooke
Components of a computer system
Key Terms
- Hardware
- Software
- Peripheral
- Network
- Human resources
- Client
- Thin Client
- Server
- DNS
- Router
- Firewall
1.2.1 Define the terms: hardware, software, peripheral, network, human resources
Term | Definition |
Hardware | The physical components of a computer system. |
Software | Programs used to operate computers and related devices. |
Peripheral | Hardware that exists outside the main system. |
Network | A computer network is a connection of computers and other hardware devices through communication channels. |
Human Resources | Human element of the computer system often known as "Meatware". |
1.2.2 Describe the roles that a computer can take in a networked world
Client
In a client server network the client computer is the computer where the end user works. It runs the applications managed by the server. Clients are generally personal computers of some kind such as those you would use on a home network. There are different classifications for servers.
Fat Client
This sort of client will perform the bulk of the processing required by the end user. A personal computer is a good example of this.
Thin Client
Client hardware and software can be streamlined in a thin client setup where the bulk of the processing and software is managed directly by the server and the thin client is little more than a screen with a computer that has a graphics card and a network card.
Server
The purpose of the server is to share such things as data, hardware or software services, internet connections etc. Servers are computers that have a high specification in terms of the hardware. There are many types of servers such as
- Data servers
- Web servers
- File servers
- Print servers
- Game servers
- Application servers
Each of the different servers will provide different services to clients in a client-server model. The operating system on a server will be different to that provided for a client or a personal computer. The hardware will vary depending on the purpose of the server.
Email server
An email server provide a digital post office for the network. Messages are transmitted to and from these servers using some or all of the following
- SMTP - Simple Mail Transfer Protocol
- IMAP - Internet Message Access Protocol
- POP3 - Post Office Protocol
These protocols determine how the mail is sent and received across the mail service. Over recent years local email servers have been hit by problems with spam. These days businesses will use a more centralised system that is more easily managed.
DNS server
The Domain Name System (DNS) is a naming system that translates domain names into IP addresses. For example the domain name google.com into http://74.125.224.72/.
The DNS is essentially a database that is distributed over several servers. Each of the DNS servers will be responsible for resolving a certain portion of the domain name. Many applications use DNS such as:
- World Wide Web (WWW)
- Instant Messaging (IM)
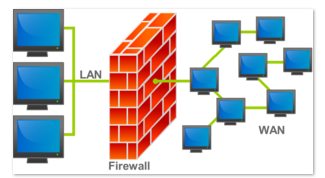
Router and firewall
Router
A router is a device that transfers data packets between networks. Common application for this are the exchange of data between a home network and the internet (via the Internet Service Provider (ISP)).
Firewall
A firewall is a network security system that monitors incoming and outgoing packets based on a set of security rules. It acts as a protective barrier between a trusted or managed network and an external or unmanaged network. A firewall is generally software based but can be a configured hardware device.
1.2.3 Discuss the social and ethical issues associated with a networked world
There are many social and ethical issues that may relate to the use of technology. [1]
Reliability and integrity
Reliability refers to the operation of hardware, the design of software, the accuracy of data or the
correspondence of data with the real world. Data may be unreliable if it has been entered incorrectly or if it
becomes outdated. The reliability of machines, software and data determines our confidence in their value.
Integrity refers to safeguarding the accuracy and completeness of stored data. Data lacks integrity when it
has been changed accidentally or tampered with. Examples of data losing integrity are where information is
duplicated in a relational database and only one copy is updated or where data entries have been maliciously
altered.
Security
Security refers to the protection of hardware, software, machines and networks from unauthorized access.
Security measures include restricted access to machines and networks for certain employees or to prevent
access by hackers. The degree of security of information systems largely determines society’s confidence in
the information contained in the systems.
Privacy and anonymity
Privacy is the ability of individuals and groups to determine for themselves when, how and to what extent
information about themselves is shared with others. At its extreme, privacy becomes anonymity when, for
instance, a person uses it to conceal his or her true identity in order to cyber-bully someone else. Conversely,
excessive privacy could also conceal the perpetrators of criminal, terrorist or computer hacking acts from
law enforcement agencies.
Intellectual property
Intellectual property includes ideas, discoveries, writings, works of art, software, collections and
presentations of data. Copyright, trademarks and patents exist to protect intellectual property. However,
the easy and accurate duplication methods made available through IT can undermine such protection.
Authenticity
Authenticity means establishing a user’s identity beyond reasonable doubt. Authenticating the user is
crucial in many scenarios, particularly in business and legal matters. A simple example of authentication is
a user login to a network. A more advanced example would be the use of encrypted digital signatures in a
business transaction or the use of watermarking on digital photographs.
The digital divide and equality of access
The growth of the use of IT systems has led to disparities in the use of, and access to, information technologies.
Disparities exist not only internationally between countries, but also within countries between different
socio-economic groups as well as within what may appear to be relatively homogenous groups. This may
lead to groups or individuals without access to IT being disadvantaged. For example, while telelearning may
bring previously unavailable opportunities to everyone’s doorstep, factors such as the cost and availability
of hardware, software or access to the internet may create a “digital divide”.
Surveillance
Surveillance is the use of IT to monitor the actions of people. For example, monitoring may be used to
track, record and assess employees’ performance. It can be used to support claims for promotion or to
ensure that employees follow the organization’s internet policy appropriately.
Globalization and cultural diversity
Globalization means the diminishing importance of geographical, political, economic and cultural
boundaries. IT has played a major role in reducing these boundaries. For example, any dramatic event
anywhere in the world can be broadcast almost instantly by television or on the internet. However, the new
“global village” may lead to the extinction of minority languages.
Policies
Policies are enforceable measures intended to promote appropriate and discourage inappropriate use
relating to information technologies. They can be developed by governments, businesses, private groups
or individuals. They normally consist of rules governing access to, or use of, information, hardware, software
and networks. For example, a school policy on the use of IT would consist of each user signing an acceptable use
policy. It would also address unlawful access to the network through, for example, identity theft or using
hacking software, and how these transgressions would be treated. Many websites also require users to
agree to specific policies before allowing access to their services.
Policies also affect the exchange of information, for example, by making it subject to copyright laws and
raising people’s awareness of plagiarism. In general, policies can promote or restrict access, guide behaviour,
require the fulfillment of certain conditions prior to or during use, or need to be developed to address
unforeseen issues such as cyber-bullying.
Standards and protocols
Standards and protocols are technical rules and conventions that enable compatibility and therefore
facilitate communication or interoperability between different IT systems and their components. They
might govern the design and use of hardware, software and information. For example, the communication
protocols used on the internet, the ASCII representations for characters, or the design of the printer port on
a personal computer are all governed by standards.
People and machines
The use of IT systems brings significant advantages, for instance in ease of use, being available 24/7, or
through its use rather than exposing humans to a potentially hazardous environment. However, this can
raise concerns about the rate at which technology is being introduced and issues that may arise from
insufficient testing in critical situations such as air traffic control. The ultimate fear of many people is that
future systems will be programmed to make decisions that would be better taken by humans, such as the
decision to deploy nuclear weapons.
There are also social impacts such as internet addiction, where people feel that they can never get away
from IT and are trapped on a “digital treadmill”.
Digital citizenship
Digital citizenship can be defined as appropriate behaviour that represents the responsible, ethical and legal approach that individuals take in any situation with respect to the use of IT. Digital citizenship permeates, in one way or another, all of the preceding social and ethical considerations. Other specific social and ethical considerations Other social and ethical considerations may emerge during different scenarios discussed in class. These may
be related to changes in attitudes towards the use of IT systems, or new developments in IT such as social networking or e-assessment.
Policies: To control how systems are used.
Authenticity: How can you prove that it is you accessing a system?
Intellectual property:
Security: Security is a big issue with so many connected devices. In smart homes, where the Internet of Things is being developed to make the way of life easier for people, there are certain types of bulbs that can be controlled with an app on your phone through wifi or bluetooth. It is possible to hack the “master bulb” (which is connected to the wifi and controls the others) and enter the victim’s wifi.
Privacy and anonymity: This has become big problem due to the fact that our devices are interconnected. Think about GPS in phones and the fact that the providers can know wherever you are in the world.
Digital citizenship: The appropriate behaviour that represents the responsible, ethical and legal approach that individuals take in respect to the use of IT.
Surveillance: The use of IT resources to monitor the actions of people.
Globalization: Outsourcing of businesses through the internet
Digital divide and equality of access: Will everyone have access to the system,
Reliability and integrity: Reliability is not usually a problem for most “important” sectors such as Facebook or social networking sites. They have to be reliable so that they offer their service full time without crashes and avoid system breaches. Integrity is a bit of a problem due to personalization on the web which can actively filter information from you so that you receive information tailored more to you.
People and machines: Loss of jobs due to computers being more efficient at some tasks
Standards and protocols:
System design and analysis
Key Terms
- Stakeholders
- Questionnaire
- Interview
- Flowchart
- Structure Chart
- Data Flow diagram (DFD)
- System Development Lifecycle (SDLC)
- Waterfall development
- Agile development
- Prototypes
- End-user
1.2.4 Identify the relevant stakeholders when planning a new system
"Stakeholders are people, groups or organisations that have an interest in or might be affected by the outcome of a project." [2] These may be the managers, designers, and end users.
Example:
Question: Who would the major stakeholders be for a project that involves designing new administrative software for a national health service?
Answer:
End user: Doctors/Nurses/hopital Administrators
Project Management: Government/Local Authorities
Project designers: Software design company
1.2.5 Describe methods of obtaining requirements from stakeholders
There are several methods for collecting data to find out ore about an existing system during the analysis stage of a project.
Questionnaire
Questionnaires can be delivered online [3] or using more traditional paper based formats. The structure and format of the questions needs to ensure the data gathered is clear and unambiguous. The questions tend to fall into two categories:
- Closed format
- Open format
Closed format questions can be multiple choice type questions. These tend to give answers that are easy to analyse and can produce useful initial statistical data. They can also be used to track peoples opinion over time.
Open format questions are harder to analyse as they lead to more open ended and prose responses but may throw up unexpected and informative material. They are not so easily analysed.
Interview
An interview is normally conducted face to face but can utilise VOIP technologies. The data gathered is in the verbal response of the stakeholder who is being interviewed. This is transcribed and kept for later analysis. Again there are several types of questions that can be utilised here in terms of closed or more open ended ones to elicit further response.
The interviews will be conducted with a number of stakeholders and can generally take place in a structured or unstructured format. Structured formats tend to have similar interview questions used for all stakeholders in order to make easier comparisons between the interviews. Unstructured interviews are more informal and may produce interesting and unexpected results.
Observation
Direct observation requires the analyst to be in situ to observe the current system working. The result is that the analyst get to know the system in an unbiased way. In some cases. The observation may be done in two ways
- Human observation where a person or people observe behaviour or the working of a system.
- Mechanical observation where the human is replaced by another device such as a camera or other relevant sensor to record data.
Gathering documents
Most organisations use documents to record communications or data on the inputs processes and outputs related to a system. The analyst can use this data to gain a good understanding of how the system works. They can also get a good idea of the amount, type and format of the data flowing in the system.
Advantages and Disadvantages of the different methods
Method of gathering information | Advantages | Disadvantages |
Questionnaire | Quick and simple way to gather a large amount of data. | Limited responses. Very dependent on good question design and analysis. Take time to fill out. |
Interview | Good face to face and may leads to finding out more than initially expected due to a two way conversation. | Can take a lot of time to conduct interviews with large group of stakeholders. |
Observation | First hand, unbiased information. | People behave differently when watched. |
Gathering Documents | Analysts can get a good objective understanding of the system. | Documents may be outdated or inconsistently stored or recorded. |
1.2.6 Describe appropriate techniques for gathering the information needed to arrive at a workable solution
Analyse inputs outputs processes. Analyse problems with current system.
Examining current systems, competing products, organizational capabilities, literature searches.
S/E Intellectual property.
1.2.7 Construct suitable representations to illustrate system requirements
System flow charts
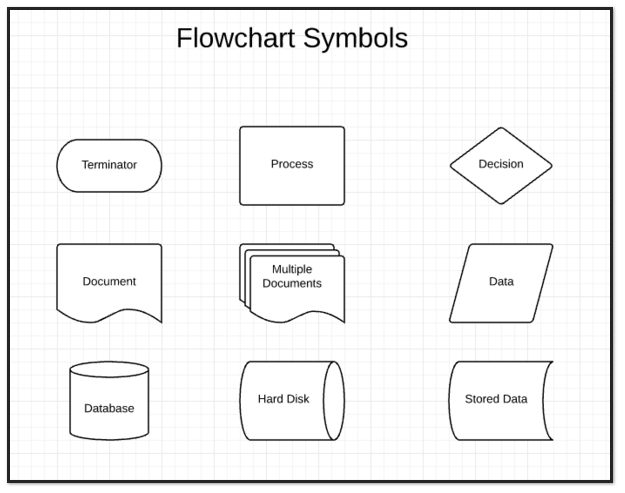
A flowchart is a diagram commonly used to represent an algorithm or a process. [4]
The can be used in a number of ways outlined below:
Sequential Structure
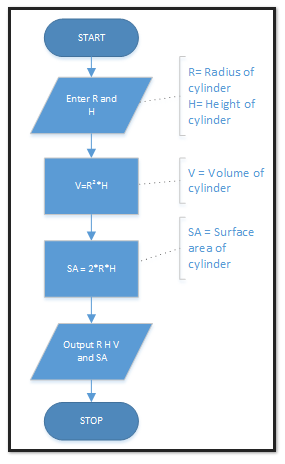
Here is a simple flowchart that shows the process to calculate the volume and surface area of a cylinder and output that along with the radius of the cylinder, the height of the cylinder and the volume of the cylinder.
Selection /Branching Structure
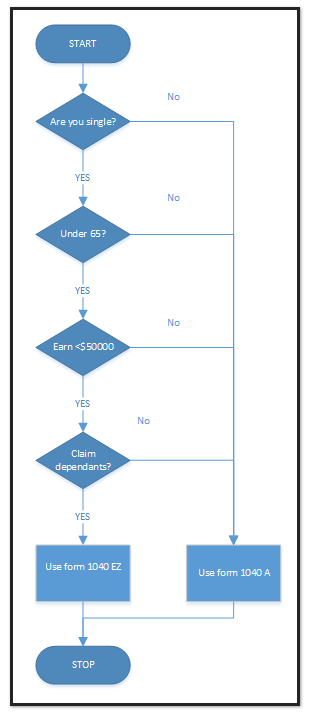
Here is a flowchart that shows how to select a form based on preset criteria.
Repetition looping structure
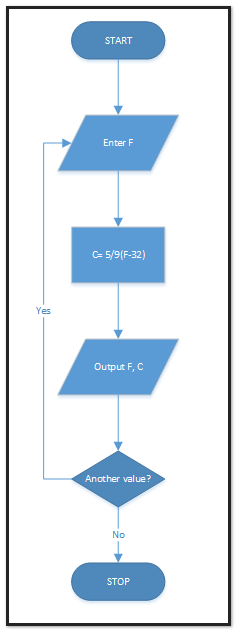
This flowchart shows a process that converts Fahrenheit to Centigrade and keeps going until the user terminates the process.
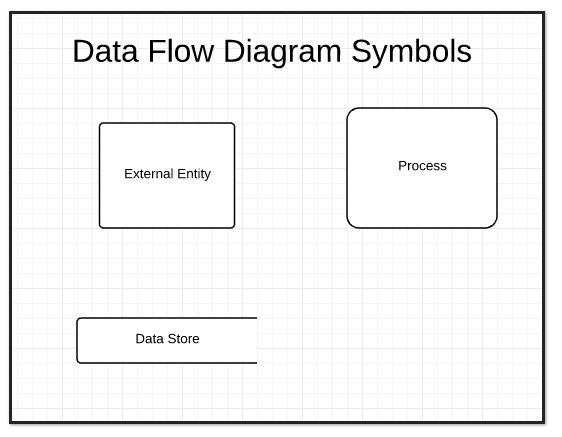
Data flow diagrams
Structure chart
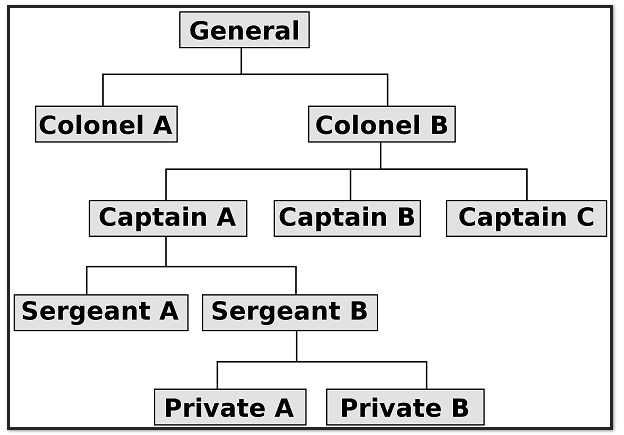
Structure charts are often used to show top down organisational structures in a tree.
1.2.8 Describe the purpose of prototypes to demonstrate the proposed system to the client
AIM 5 The need to effectively collaborate to gather appropriate information to resolve complex problems.
AIM 6 To develop logical and critical thinking to develop proposed systems.
1.2.9 Discuss the importance of iteration during the design process
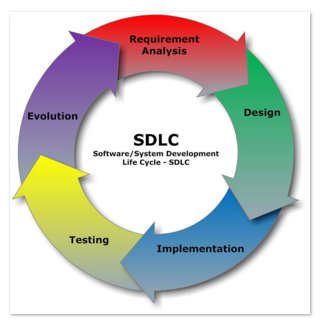
System Design Life Cycle
The System Development Life Cycle (SDLC) is the process from the very beginnings of an idea alll the way through to the delivery of a final product to a client. The cycle represents to continuing maintenance of the system throughout its life. This maintenance stage is often the largest part of the process in terms of cost.
There are variations of the naming of the elements of the cycle. The stages of the SDLC as analysed in greater detail in various sections in this unit as seen above.
Development Approach
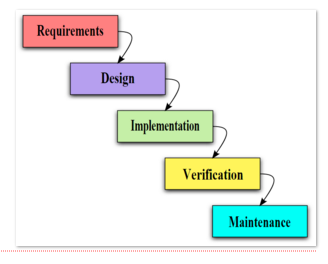
The SDLC can be approached in a variety of ways. There are know as development models. The most traditional approach has been the waterfall model. This follows the stages of the design lifecycle but in a linear fashion where one stage follows another and each stage is considered for the whole project.
Waterfall Model
With this method each stage is rarely revisited. It is a costly document heavy method that is best used on big projects that require a lot of management and where there are not likely to be any major changes in requirement by the client. There are a number of disadvantages with this model that make it unsuitable for software development:
- as requirements are made at the beginning no room for mistakes
- project communication with the client is limited
- team members may be idle for large amounts of time
- very rigid structure does not allow changes to be easily made
- more time consuming
The agile development model seeks to address some of these weaknesses by providing a more adaptable model.
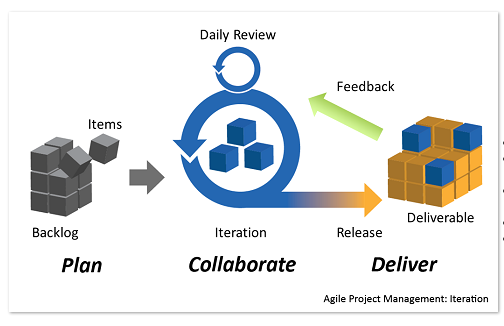
Agile development model
The agile model uses the same stages as the SDLC but the agile model focuses on delivering workable solutions to small elements of the project over short stretches of time. This approach is more commonly applied to projects such as software design. The advantages fo this system are:
- adaptive teams that respond to change
- constant and effective communication means no ambiguity
- documentation is minimal and direct and saves time
- time saving
- well suited to software and web design projects
1.2.10 Explain the possible consequences of failing to involve the end-user in the design process
The failure to involve the end-user may lead to software that is not suitable for its intended use, which may have adverse effects on user productivity. End users can be consulted formally in a number or ways throughout the lifecycle.
They may be initially consulted in the analysis stage as part of a data gathering exercise in order to draw up the performance criteria or to examine the problems with current systems. Failure to involve them here may lead to a product that does not have the correct criteria for success leading to a project that does not provide for the end user.
End users may also be consulted as part of an alpha or beta testing program. Alpha testing is predominately in house but may involve friends or family and emulates a high proportion of users. Good alpha testing tests the products against the basic benchmarks set down in the SDLC.
Beta testing allows the end user to explore all elements of a product that is "completed". Failure to involve the end user here will mean that a product may be released with bugs and the designers may not have a good idea what the end user thinks about the product or the extent of the usability of the product.
Throughout the process there is a need for effective collaboration and communication between the client, developer and end-user.
1.2.11 Discuss the social and ethical issues associated with the introduction of new IT systems
Refer to the social and ethical issues described above in 1.2.3.
Human interaction with the system
Key Terms
- Usability
- Accessibility
1.2.12 Define the term usability
Usability refers to the ease of use of a man made object. In computer science this can refer to hardware or software. Often the usability of an object is studied in order to ascertain whether it is:
- Easy to learn
- Satisfying to use
- Efficient to use.
1.2.13 Identify a range of usability problems with commonly used digital devices
There are many common usability issues that need to be taken account of in the design of digital devices such as the following.
- 7+- Principle.[5]
- 2-Second-Rule
- 3 click rule
- 80/20 rule
- Interface design rules
- Inverted pyramid
https://www.smashingmagazine.com/2007/10/30-usability-issues-to-be-aware-of/
Example:
Question: Can you think of a some relevant usability problems with the following devices?
Personal computers
RSI form excessive use
Mouse not suitable for left-handers
Operating system not user friendly
Cell phones
Screen size to small
Battery life too short
Keyboard (onscreen or on device) to small
Digital Cameras
Buttons too small
Hard to understand menu system
Insufficient storage
Battery life
Hard to sync with other devices
MP3 players
Buttons too small
Memory too small
No view screen
Not weather proof enough
Durability
Game consoles
Can't play older games
Learnability of some games to hard
Controls too small/big
1.2.14 Identify methods that can be used to improve the accessibility of systems
1.2.15 Identify a range of usability problems that can occur in a system
1.2.16 Discuss the moral, ethical, social, economic and environmental implications of the interaction between humans and machines
Now test yourself!
https://quizlet.com/121434678/test/embed
References
[1] IBDP, 2010, ITGS Guide, International Baccalaureate Organisation
[2] PRINCE 2 - https://www.prince2.com/blog/how-to-identify-stakeholders/
[3] Survey Monkey - https://surveymonkey.com/
[4] SEVOCAB - http://pascal.computer.org/sev_display/index.action
[5] The Magical Number Seven, Plus or Minus Two: Some Limits on our Capacity for Processing Information - http://psychclassics.yorku.ca/Miller/